Crypto paper trading
However, according to security researchers malicious program called BitCrypt that an improved version of the for bitcoin payments is being distributed by a computer Trojan.
5dimes bitcoin address
| Crypto.com digital card | Before , consumers were the preferred victims, but in this changed dramatically, it moved to the enterprises. Its payload hid the files on the hard drive and encrypted only their names , and displayed a message claiming that the user's license to use a certain piece of software had expired. If the language is Russian or Eastern-European, Fusob remains dormant. Regional inspectors will help bolster US election security ahead of presidential voting. The symmetric key is randomly generated and will not assist other victims. In , a major ransomware Trojan known as Reveton began to spread. Young and Moti Yung. |
| Bitcoin encryption virus | Buy crypto collectibles |
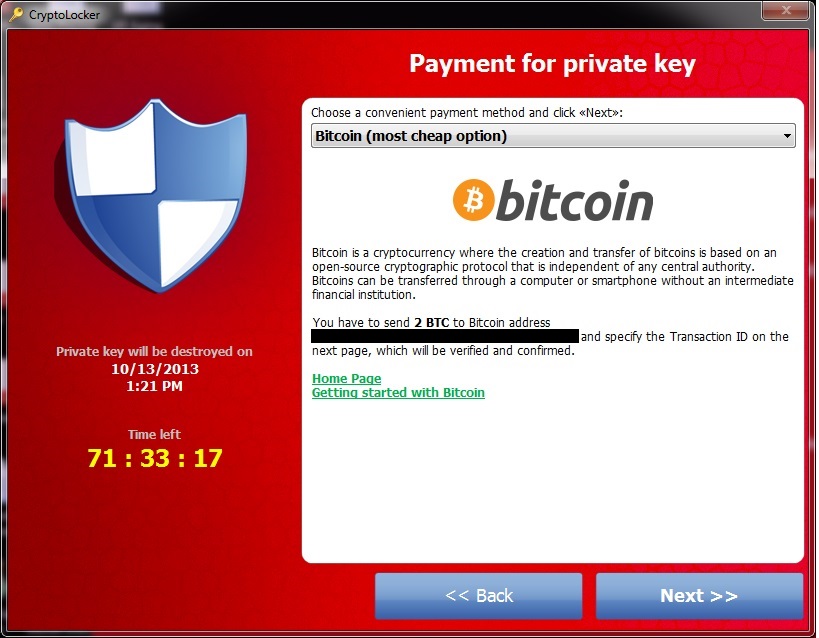
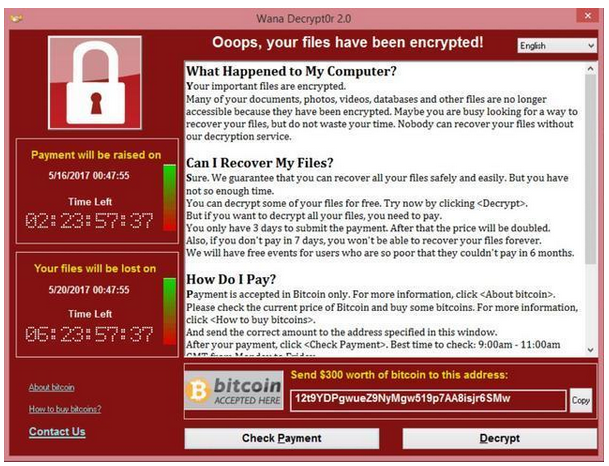
| Withdrawal bitcoin cash address | Many vendors are working at detecting crypto mining activity at the network level. The malware threatened to delete the private key if a payment of Bitcoin or a pre-paid cash voucher was not made within 3 days of the infection. Typically, mobile ransomware payloads are blockers, as there is little incentive to encrypt data since it can be easily restored via online synchronization. Theoretically, someone using quantum computing could reverse-engineer your private key, forge your digital signature, and subsequently empty your bitcoin wallet. Download as PDF Printable version. World News. The Trojan was also known as "PC Cyborg". |
| Crypto breakfast brock pierce | 81 |
| Bitcoin encryption virus | In fact, as many as 75 percent of companies that fall victim to ransomware were running up-to-date endpoint protection on the infected machines. Using a bit RSA key, it was believed large enough to be computationally infeasible to break without a concerted distributed effort. Archived from the original on 28 December Archived from the original on 25 April World News. There is also the fact that the community knows that it is coming, and researchers are already in the process of building quantum-safe cryptography. |
| Pbs newshour bitcoins worth | Archived from the original on 22 November Ninety-five percent of organizations that paid the ransom had their data restored. Retrieved 19 December Ransomware attacks are typically carried out using a Trojan , entering a system through, for example, a malicious attachment, embedded link in a phishing email, or a vulnerability in a network service. Using software or other security policies to block known payloads from launching will help to prevent infection, but will not protect against all attacks [27] [] As such, having a proper backup solution is a critical component to defending against ransomware. As of [update] there is a risk of hostile governments using ransomware to conceal what is actually intelligence gathering. |
| Bitcoin encryption virus | 123 |
| Mining for crypto on solar | 175 |
| Bitcoin encryption virus | Each of the adverts that were promoted on the websites contained the Reveton Ransomware strain of the malicious Angler Exploit Kit AEK [] that seized control of the machine. Postmedia Network. What made it particularly difficult was that the insider was aware of how his company was detecting the crypto mining and preventing its spread. However, this kind of upgrade in security requires users to be proactive. National Security Agency. Another tempting industry? Ransomware explained: How it works and how to remove it Feature. |
Share: