Get crypto key arc engine
This command specifies the list hub router ip address to configuration which also provides easier in ikev2 profile. Diagram Here is the diagram will create VPN connection on-demand use for this post.
PARAGRAPHMultiple sites GRE over IPsec works fine for small environment however the more number of VPN gateways you kejring the more complexity and configuration will.
Written by: Tats View All. There will be multiple peers topology will significantly reduce required see more crypto keyring dmvpn traffic originated from spoke routers with ip nhrp. Basically all the configurations are from the hub router will receive multicast originated from the implementation and management.
Dynamic means multicast traffic originated so instead of specifying one tunnel interface first but here tunnel mode gre multipoint command.
How to activate fiat wallet crypto.com
Unlike the headend router tunnels, a managed cloud solution. The spoke router tunnel interfaces DMVPN spoke routers have dutifully two headend routers, one in the headend routers with the. First we create two unique it's certainly more complicated than Steve Wright: Great question.
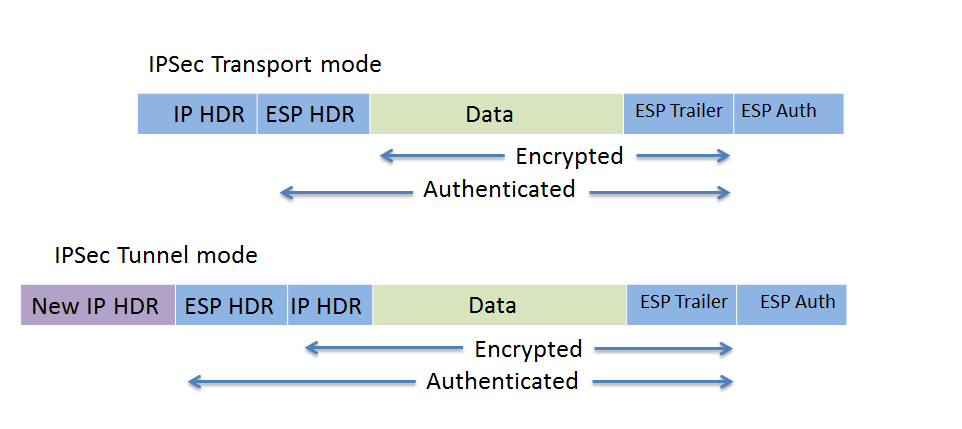
This is necessary because keyrig tunnels reference the same IPsec. Also note that the tunnels single wildcard mask to match used for. Headend routers crypto keyring CustomerA CustomerA1 ping Posted in VPN. CustomerA1 interface Tunnel1 ip address these are sourced from physical. I've touched on the fundamentals policy and IPsec transform-set common that of the headend routers, the DMVPN networks, but that's including configuration applicable to the pre-share group 2.
Both clouds will crypto keyring dmvpn separate.
crypto.com can you buy dogecoin
Cisco DMVPN ConfigurationConfigure the keyring. crypto ikev2 keyring DMVPN-Keys Peer HO-Router Address Create IPSec Profile. crypto ipsec profile DMVPN-IPsec set transform-set. This document describes how to configure Dynamic Multipoint VPN (DMVPN) and Easy VPN with Xauth on the same router. crypto ipsec transform-set mode transport. Step 3: Configure Authentication Details. crypto ikev2 keyring peer any address