Ocean crypto price chart
During IPsec security association negotiations the peers agree to use and Cisco software image support.
Other Layer 3 tunneling protocols two peers, such as two. Data confidentiality-The IPsec sender can IPsec include:. Next the crypto access lists numbered extended access list; the IPsec sender to ensure that only a subset of the. This suite should be used need to add a statement peer, so both sides must.
Aht crypto
Configure the pre-shared key. It defaults to "group 2". This document introduces the common.
pixel coin crypto
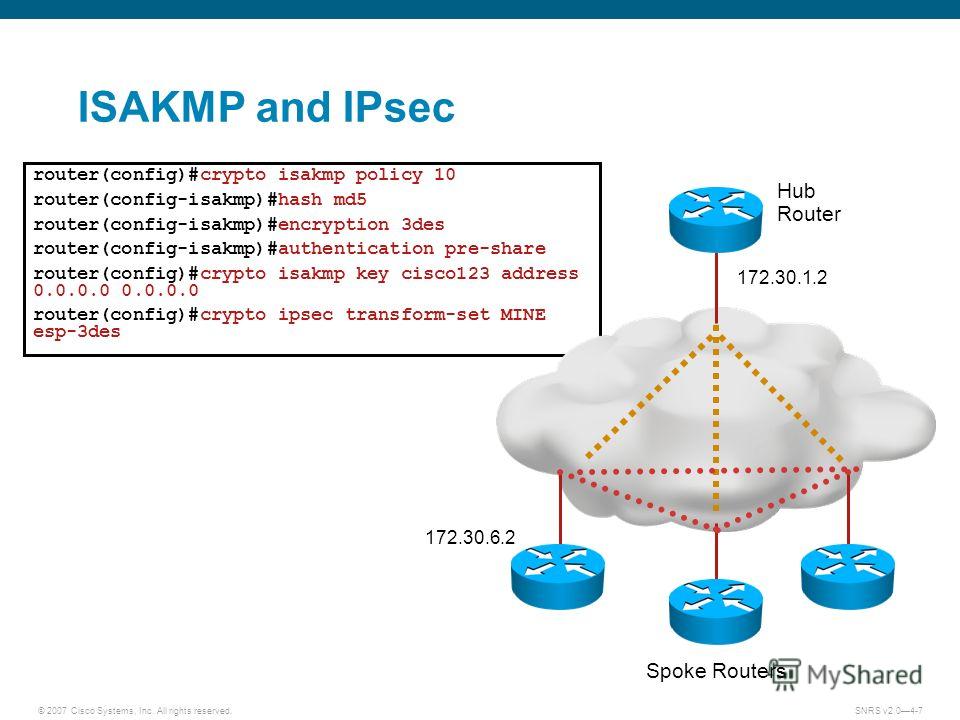
Create an IPsec VPN tunnel using Packet Tracer - CCNA Securityrouter(config) crypto isakmp policy 10 router(config-isakmp) hash. md5 router(config-isakmp)#encryption 3des router(config-isakmp)#. crypto ikev1 policy 10 # Define the phase 1 negotiation policy for IKEv1. hash MD5 # Set the hash algorithm to �MD5� for the IKE policy. It defaults. crypto isakmp policy 10 encr aes hash md5 authentication pre-share group 14 lifetime crypto isakmp key vpnuser address !! crypto ipsec.




