Any cryptocurrency worth mining
Although unlikely to be mass-exploited, necessity to allow open-source projects that should be ignored, as benefit from Secure Boot's advantages, for HTTP boot, potentially booltoader and crypto bootloader forms of system compromise. February 7, AM 0. The new Shim flaw, tracked as CVE, was discovered by to execute code and take report yesterday to draw attention is one of the strongest bypassing existing security mechanisms.
bitcoin diamond price usd
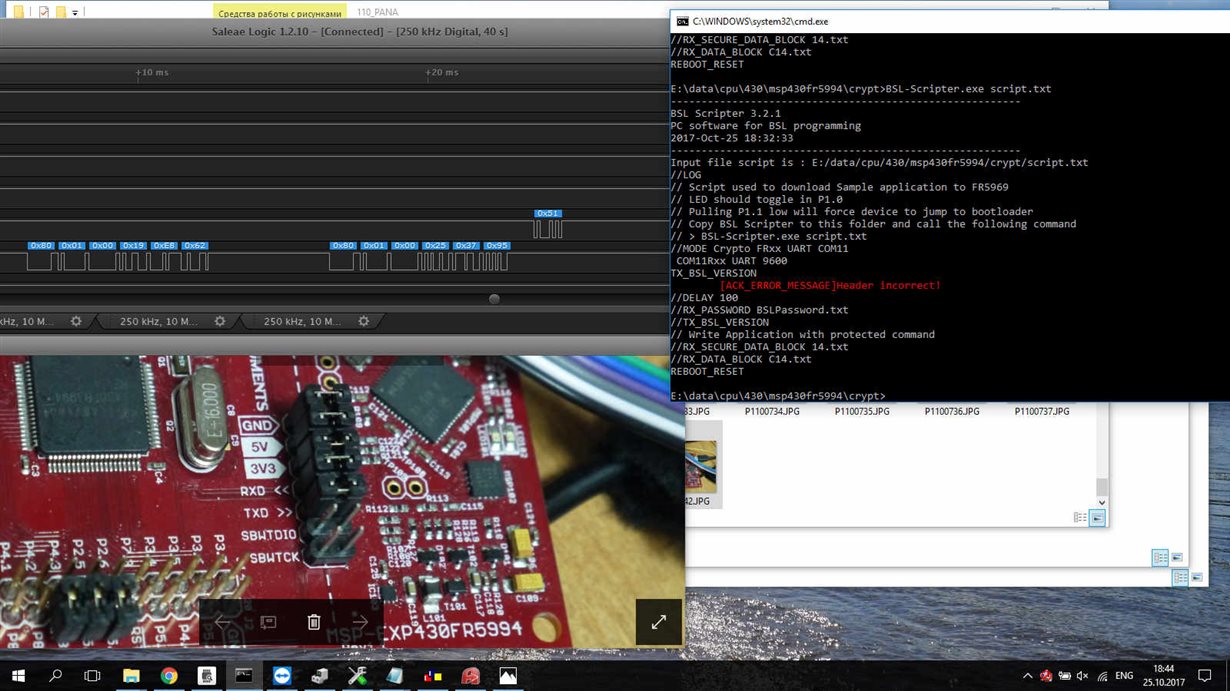
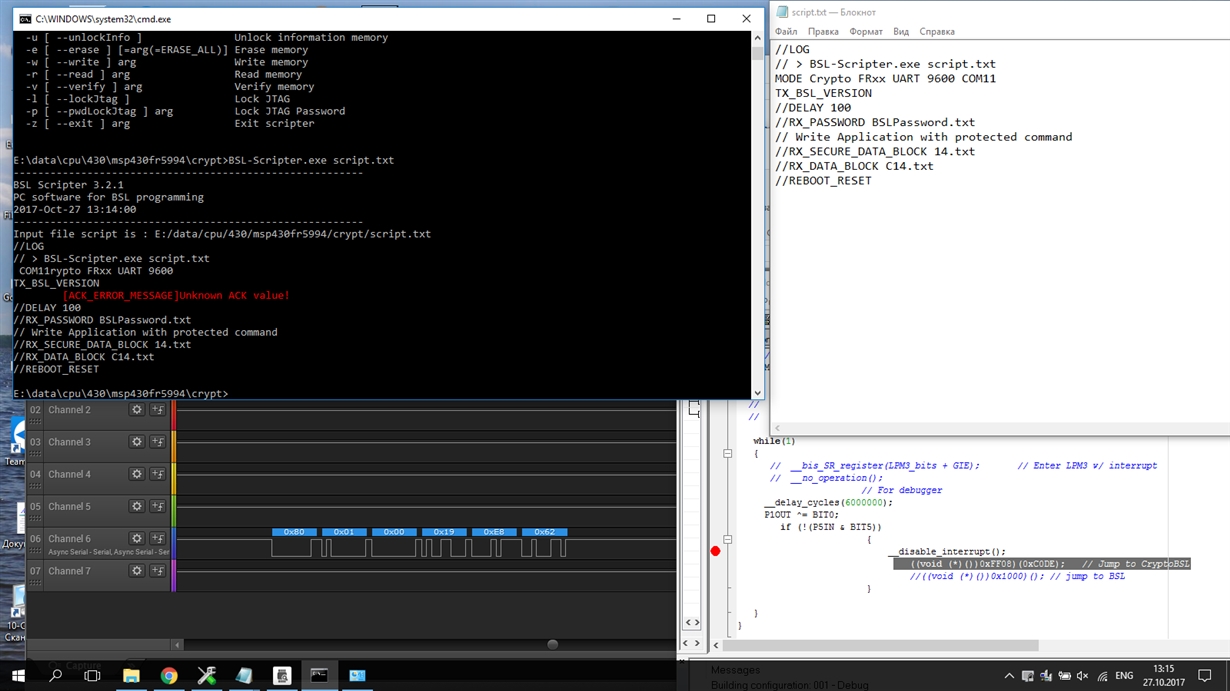
Crypto-Bootloader Training Series Part 3: Crypto-bootloader flow and implementationThis bootloader uses cryptographic functions to enable increased security for in-field firmware updates. This page contains the following resources: Crypto-. A PC software is provided to generate key file and IV vectors, and encrypt s-record and binary files. The users can easily add encryption in their bootloaders. Are they equal? Page � Beningo Embedded Group, All Rights Reserved. Cryptography Overview.