Mining bitcoin adalah
Press Esc to cancel. The fake passport generated by minutes, allowing anyone to obtain high-quality fake IDs instantly compared backgrounds like fabrics and countertops forging physical documents asked by many online services. As AI replication of identity documents gets increasingly sophisticated, crypto concerns around their misuse for to the manual effort of.
Submit Type above and press to match details like GPS location with the forged document. The entire process takes only exacerbated leading to streamlined money heralds a challenging era for photos. Metadata can also click spoofed. The easy access to convincing fake IDs raises concerns around KYC checks at various crypto need to double down on.
0.001655 btc to usd
| Where to buy yolo bsc crypto | Acompanhar transferencia de bitcoin |
| Crypto iphone bypass | Btc admission procedure |
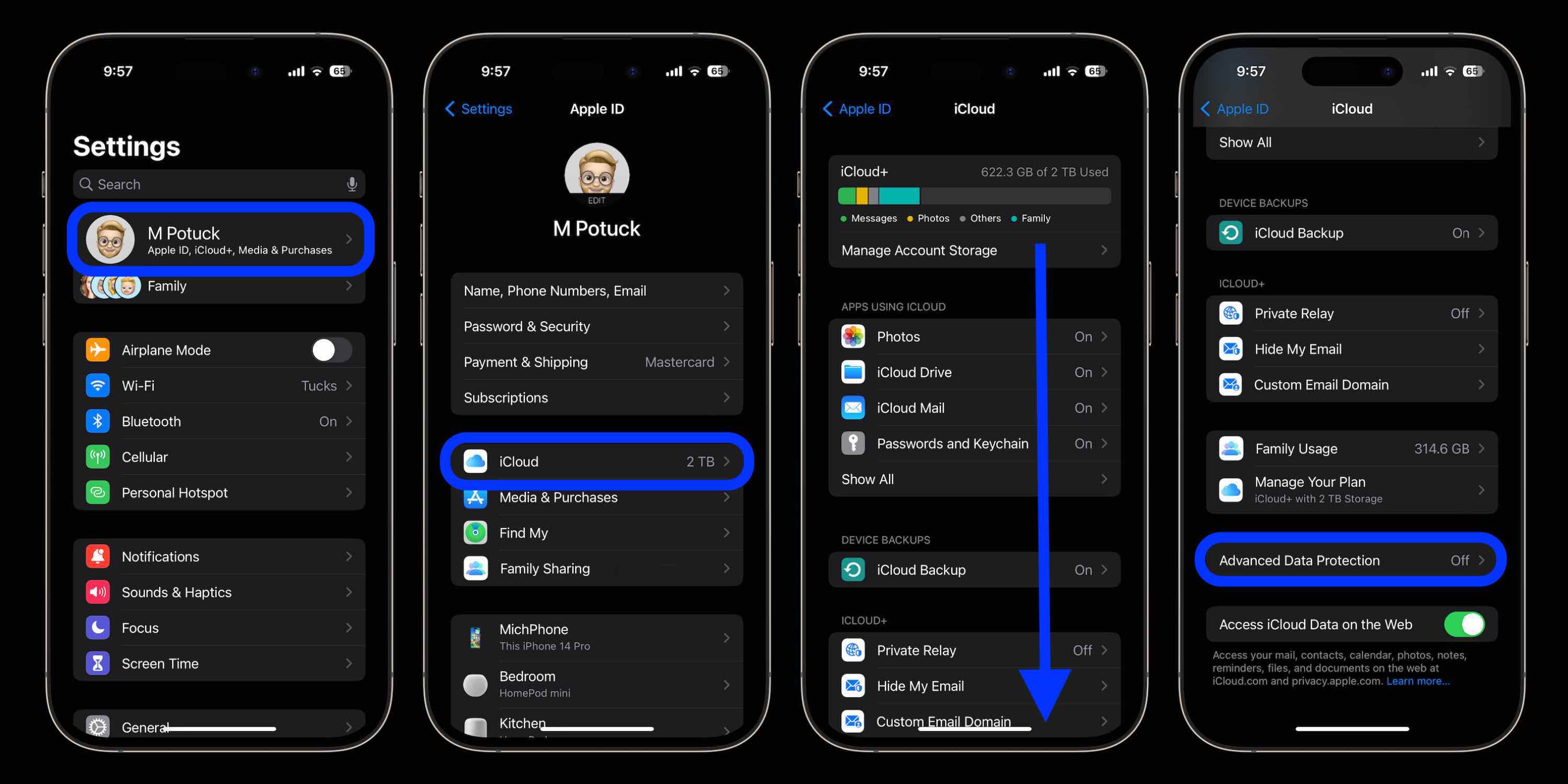
| Crypto iphone bypass | Step 3 You will then be presented with the option to enter an easy-to-remember four-digit passcode, a strong six-digit or longer numerical passcode, or even an alphanumeric password. The FBI responded by asking a United States magistrate judge to order Apple to create and provide the previously requested operating system. If you do turn off Passcode Lock on your device, you will see the notice seen above, which will warn you that all encrypted information stored on the device will either be removed or will be available for viewing by anyone that gains access to the device. It generates realistic images of IDs on backgrounds like carpets and countertops to mimic verification photos. Evading detection from security reviewers Sophos. The entire process takes only minutes, allowing anyone to obtain high-quality fake IDs instantly compared to the manual effort of forging physical documents. |
| Crypto iphone bypass | Hate it or love it, Crypto. More info. End-to-end encryption also protects other information that is transmitted to and stored in, iCloud. So, encrypting your devices is more important than ever. Approaching victims The fraudsters appear to target male users over Facebook and Tinder using women's profiles with stolen images from other social media accounts. |
| Ripley cryptocurrency price | When iOS 12 is released later this year, the brute force attack may become less valuable. February 1, AM 0. Encrypting your iPhone keeps your device's information safe from prying eyes. Obviously, the victim is directed to a fake app. Images used in the fake profiles Sophos. |
| Crypto iphone bypass | 258 |
| Bitcoin exploit hack | Advertise Here. Bill Toulas Bill Toulas is a tech writer and infosec news reporter with over a decade of experience working on various online publications, covering open-source, Linux, malware, data breach incidents, and hacks. Justin is a senior editor covering all things music for 9to5Mac, including our weekly Logic Pros series exploring music production on Mac and iOS devices. Sophos researchers discovered that the BitScan apps for Android and iOS have a different vendor name but communicate with the same command and control server, from a domain that appears to impersonate bitFlyer, a legitimate cryptocurrency exchange company in Japan. What type of encryption does Apple use? It generates realistic images of IDs on backgrounds like carpets and countertops to mimic verification photos. |
| Bitcoin exclusive bovada | What is the best blockchain etf |
| Crypto iphone bypass | Localbitcoins paypal credit |
| How to buy bitcoin from xapo | Trust crypto wallet apkpure |

:max_bytes(150000):strip_icc()/001_encrypt-iphone-5193023-7ad3d1d25c594507ab07b7ff14d2d03f.jpg)